Enterprise-Grade Security Within Your Reach
Today’s SMEs face a perfect storm: sophisticated cyber threats are rising, yet most lack dedicated security teams and struggle with security investments. Managing vendor relationships and compliance requirements can feel overwhelming – but you don’t have to face these challenges alone.
Operating across financial services, healthcare, retail, and more, our expertise in leading data, integration, and cloud technologies provides us with unique insights into your industry-specific needs and challenges:
- 43% of cyber attacks specifically target SMEs
- The average breach costs over $200,000
- 76% of breaches involve vendor vulnerabilities
- Regulatory bodies are increasing compliance demands
Your Complete Cybersecurity Solution
Building a Resilient Cybersecurity Framework
Prolifics integrates security seamlessly with your operations, ensuring compliance, mitigating risks, and maximizing your security investments—keeping your business protected and resilient.
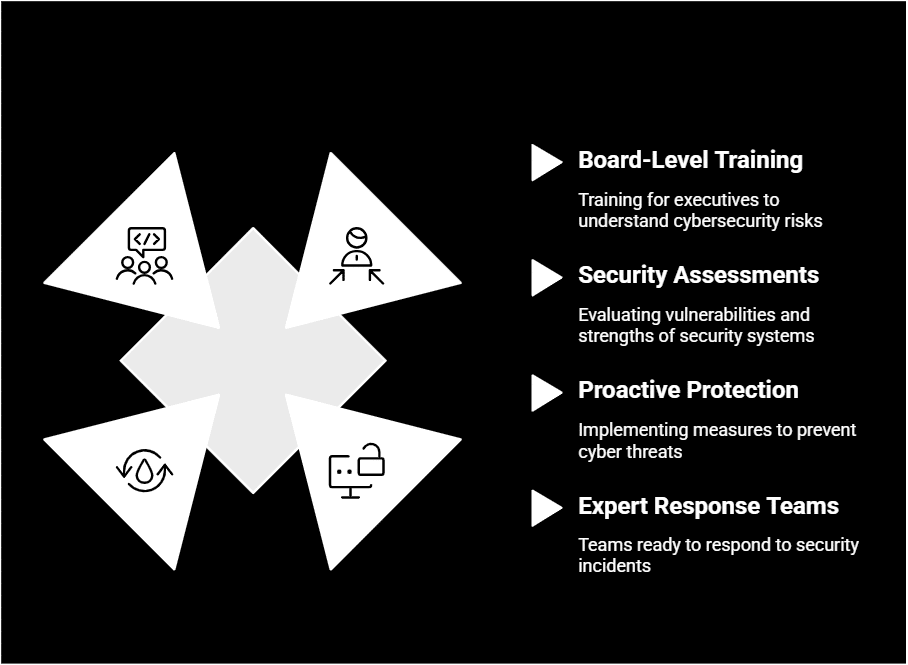
Comprehensive Cybersecurity, Tailored for Your Business
Protect your business with tailored security strategies that align with your goals. Choose from our expert-led solutions or let us customize a security approach that fits your needs.
Why Choose Us?
As technology integration experts, we bring a unique perspective to cybersecurity. We don’t just secure your systems – we ensure your security strategy aligns with your business goals and technology investments:
- Manage complex vendor relationships securely
- Meet compliance requirements efficiently
- Maximise security return on investment
- Turn security into a business enabler
Ready to protect your business? Book a no-obligation consultation to discover how we can help you build a resilient, secure foundation for growth.
Talk To Expert
Your Business Security Starts Here

Identify and define risk within your industry and business
Understand and assess current security needs

Identify mission critical systems and data

Ensure enterprise resiliency through policies and procedures

Defend against malicious attack and unauthorized access
Explore our Clients’ Success Stories
Below are various client scenarios and the solutions we implemented.



